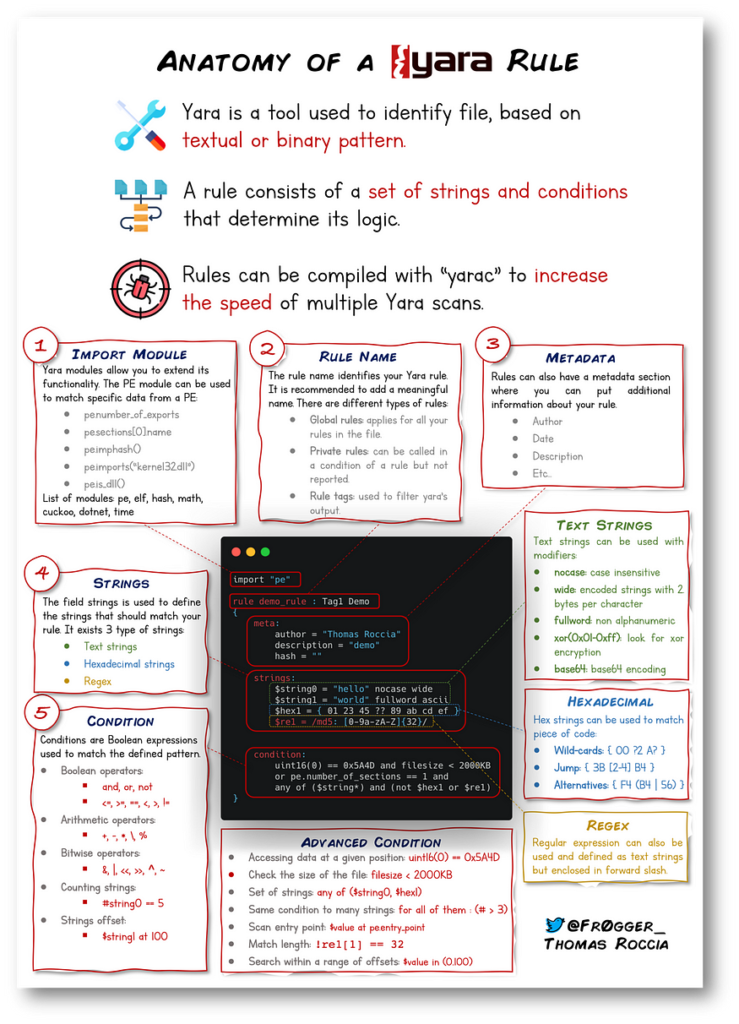
CIA Triad: Where Cybersecurity Begins
When it comes to cybersecurity, everything begins with the CIA Triad — a fundamental framework that outlines the three core principles of information security: Confidentiality, Integrity, and Availability.
Whether you’re just getting started in infosec or brushing up on the basics, the CIA Triad is your foundation. Let’s break it down.
🕵️♂️ Confidentiality
Confidentiality ensures that sensitive data is only accessible by those who are authorized. It’s about keeping secrets safe and secure — like your personal info, login credentials, or company trade secrets.
Threat: Unauthorized Disclosure — when private data falls into the wrong hands.
Real-world Defenses:
Identity and Access Management (IAM) | Multi-Factor Authentication (2FA) | Data Encryption
🧬 Integrity
Integrity is all about trusting the accuracy of data. It means that information remains unchanged unless it’s updated by an authorized user — and any tampering can be detected.
Threat: Alteration — modifying files, records, or configurations without permission.
Real-world Examples:
A hacker changing payroll amounts
🌐 Availability
Availability makes sure your systems, apps, and data are accessible when needed. No one wants to be locked out or stuck waiting during an attack.
Threat: Denial — when services are deliberately made inaccessible, usually through attacks like DDoS or ransomware.
Real-world Defenses:
Load balancing | Redundancy and backups | DDoS protection services
💡 Why It Matters
The CIA Triad isn’t just theory — it’s the DNA of every cybersecurity control, strategy, and policy. From securing cloud apps to writing firewall rules, everything maps back to Confidentiality, Integrity, or Availability.
If you ever feel overwhelmed in security, just ask: “Which part of the CIA Triad am I protecting?”
Cybersecurity might seem complex, but it all starts with a simple triangle. Mastering the CIA Triad gives you a strong foundation in the world of infosec — whether you’re just getting started or already deep in the game.
I started this blog as a space to share my knowledge and everything I’m learning about cybersecurity — one post at a time. Stay tuned, and hopefully it won’t be too boring for you!