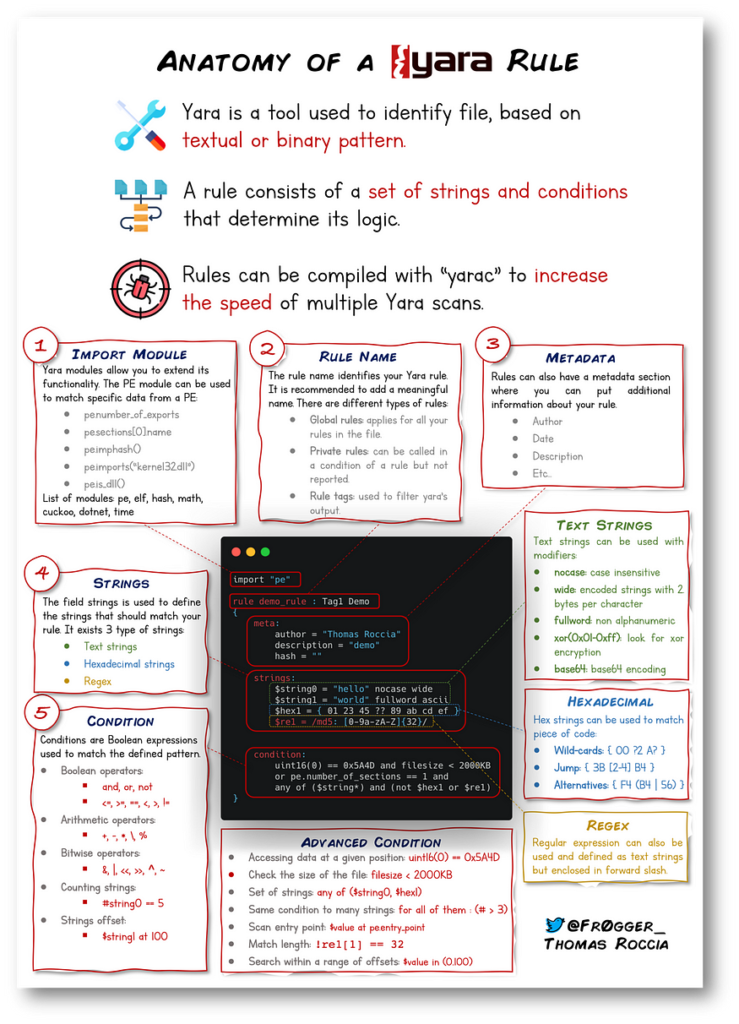
YARA, the Threat Pattern Hunter
YARA rule cheatsheet from information security researcher fr0gger_ What is YARA YARA, which stands for “Yet Another Recursive...
Simple Reverse Engineering
What is Reverse Engineering? Reverse engineering is the process of analyzing a product, system, or software to understand...
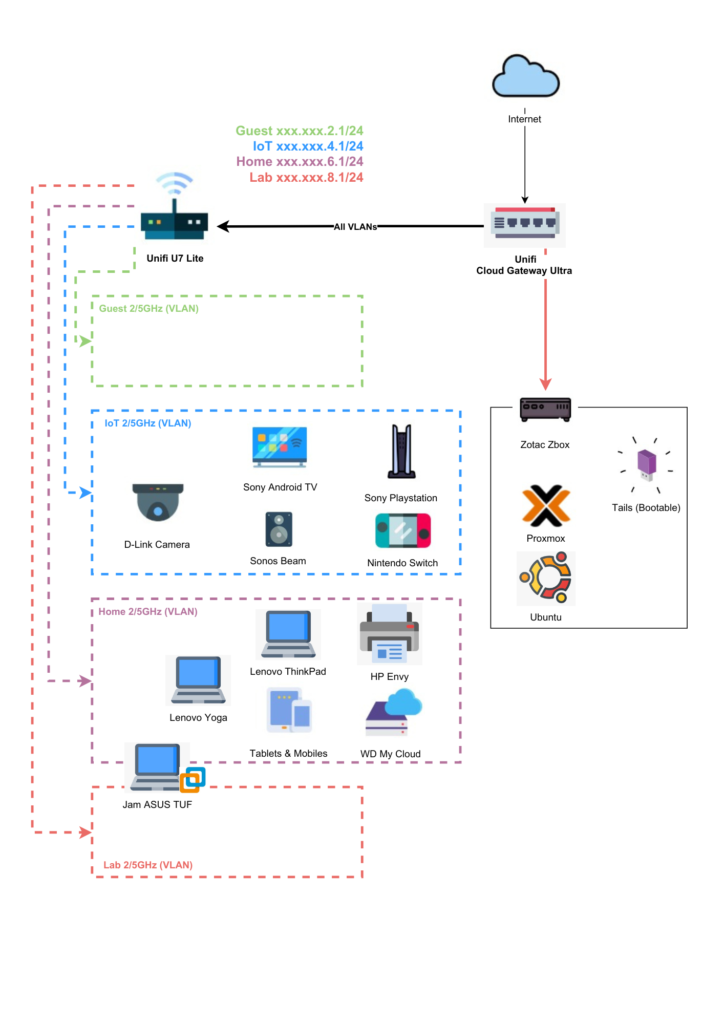
Introducing my Home Lab
Home Network & Segregation – Why It Matters More Than You Think There’s no way you’d go the...

Asymmetric Encryption
While symmetric encryption uses only one key, and you would need to share the key with others, asymmetric...

My OSCP+ Exam
My version of the r/oscp subreddit story “I passed OSCP+ on my first attempt” When I pick up...

