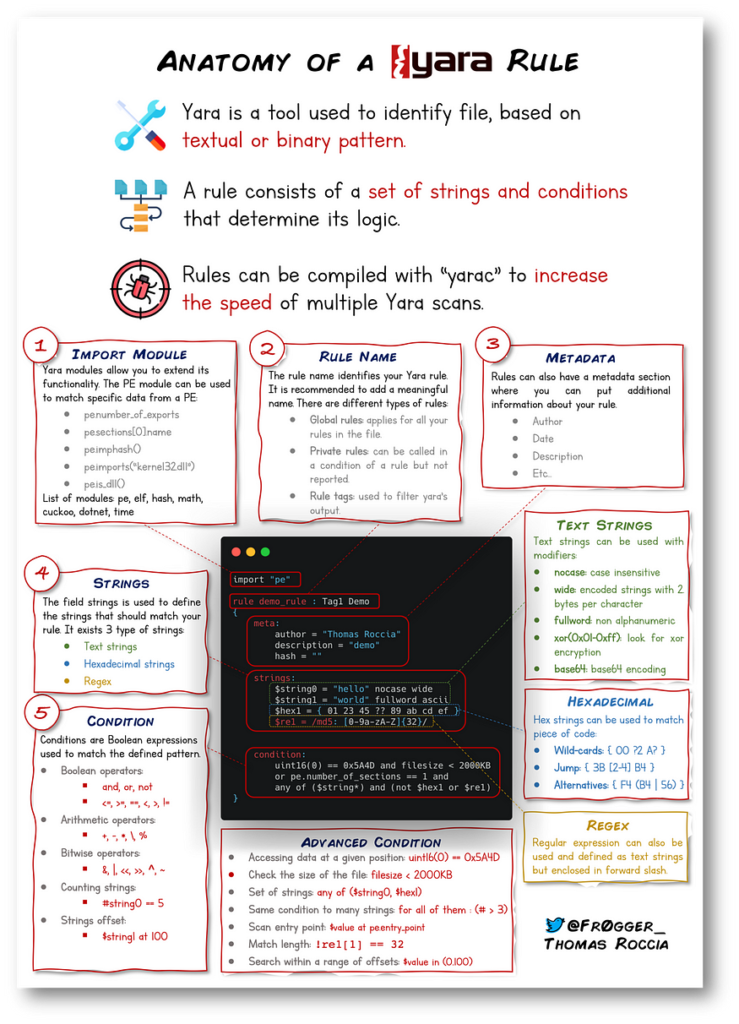
While symmetric encryption uses only one key, and you would need to share the key with others, asymmetric encryption introduces a much more secure method that eliminates the need for sharing secret keys. In this method, two different keys are used: one for encryption and the other for decryption. But how does it work, and why is it so crucial for our online security today?
What is Asymmetric Encryption?
Asymmetric encryption, also known as public key cryptography, is a method of encrypting and decrypting data using two different keys:
A public key — This key can be freely shared with anyone, allowing anyone to encrypt messages to you.
A private key — This key is kept secret by the owner and is used to decrypt the messages encrypted with the corresponding public key.
The Key Concept:
In asymmetric encryption, whatever one key encrypts, the other key can decrypt. This is the fundamental principle that powers secure communication, identity verification, and more.
Asymmetric Encryption Example: Secret Message
Let’s meet two users:
• Aokiji wants to send Kizru a message. “Meet me at 10 AM tomorrow.”
• They use asymmetric encryption, but in two(?) different ways to achieve different goals.
CASE 1. Confidentiality — Keeping the Message Secret
Goal: Only Kizaru should be able to read the message Aokiji sends.
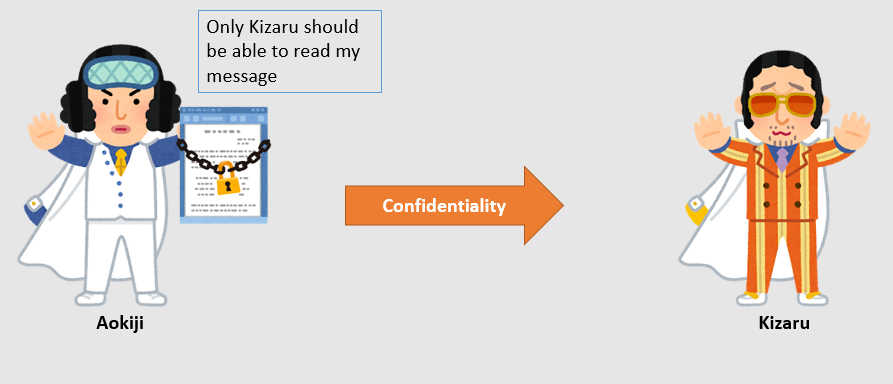
Steps:
1. Kizaru shares his public key with Aokiji.
2. Aokiji writes a secret message and encrypts it using Kizaru’s public key.
3. Aokiji sends the encrypted message to Kizaru.
4. Kizaru receives the message and decrypts it using his private key.
Result:
• Only Kizaru can decrypt it — because only he has his private key.
• Even if someone intercepts the message, they can’t read it.
It is the case we use the asymmetric encryption for confidentiality.
CASE 2. Authenticity — Verifying Who Sent It
Goal: Kizaru should know the message was definitely sent by Aokiji
Steps:
1. Aokiji encrypts the message with his private key.
2. He sends this encrypted message to Kizaru.
3. Kizaru uses Aokiji’s public key to decrypt it.
Results:
• If it successfully decrypts with Aokiji’s public key, that proves: The message could only have come from Aokiji. Because no one else could have created that encrypted message unless they had Aokiji’s private key.
But here’s the problem: since so many people in the Marines have Aokiji’s public key, they can all decrypt the message—so it’s no longer a secret.
But don’t worry, there’s a fix. We can still use asymmetric encryption—this is where the idea of digital signatures comes in.
CASE 3. Confidentiality & Authenticity & Integrity — Lock It, Sign It, Trust It
Goals:
• To prove Aokiji sent it (authenticity)
• AND keep it secret (confidentiality), and no one can change the message (Integrity)

Step-by-step:
1. Aokiji signs the message:
• he creates a hash of the message. (Not quite sure what hashing is or how to hash a file? No worries—just drop me a message, and I’ll happily walk you through it!)
• he encrypts the hash using his private key, and it is = his digital signature.
2. Aokiji encrypts the message + signature with Kizaru’s public key.
• Now only Kizaru can decrypt it.
3. Aokiji sends this encrypted bundle to Kizaru.
4. Kizaru San:
• Uses his private key to decrypt the message bundle.
• Separates the signature and the message.
• Uses Aokiji’s public key to verify the signature (by decrypting the hash).
• Hashes the message himself and compares it with the decrypted hash.
Final Result:
• Only Kizaru can read it (confidentiality via Kizaru’s public key).
• Only Aokiji could have signed it (via Aokiji’s private key),
• If both hashes match, it means the message really came from Aokiji and that no one has tampered with it—authenticity and integrity confirmed.
•Things Done.
Summary:
Asymmetric encryption uses two keys—a public key for encryption and a private key for decryption—to secure communication without sharing secret keys. Through the 3rd case with Aokiji and Kizaru, they explain how this method ensures both confidentiality and authentication. It also introduces digital signatures, which combine encryption and signing to keep messages private, verify the sender’s identity, and ensure nothing was altered in transit.